The app for independent voices
When Openness Becomes a Weapon: China’s New AI Strategy
If China can open-source frontier-level AI faster than the U.S. can regulate or contain it, what happens to the balance of technological power?
Kimi K2 is an open-source “thinking” model (agentic, tool-using) from Chinese startup Moonshot AI that reportedly outperforms leading American proprietary systems like OpenAI’s GPT‑5 and Anthropic’s Claude Sonnet 4.5 on select benchmarks.
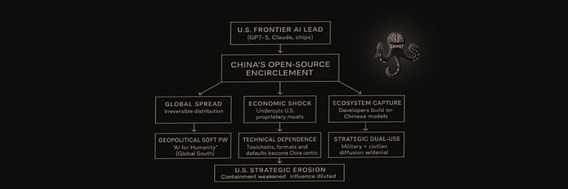
When a Chinese startup releases an open-source model that beats GPT-5, it’s not just a technical achievement—it’s a geopolitical play. Open-sourcing frontier AI allows China to bypass U.S. export controls, undermine closed-source business models, and rapidly spread its technological influence across the world. Instead of competing model-to-model, China is competing by rewiring the global ecosystem: flooding developers, startups, universities and the Global South with high-performance, low-cost AI that no Western lab is willing—or allowed—to open.
This strategy weakens Silicon Valley’s economic moat, erodes U.S. containment, and cultivates a global developer base trained on Chinese architectures. It also positions China as the “AI for Humanity” provider—an attractive counter-narrative to Western corporate gatekeeping. If scaling laws plateau, this approach becomes even more powerful: the world innovates on top of Chinese technology, not American. Open-source becomes a Trojan horse—one that encircles, rather than confronts, U.S. dominance.
Seen from a distance, China’s open-source strategy operates less like a sudden breakthrough than a slow, methodical tightening of the ring. The release of a frontier-class model into the wild triggers three broad currents: global spread, economic shock, and ecosystem capture. Once such a model circulates freely, it becomes effectively permanent, drawing governments and universities—especially in the Global South—into China’s gravitational field. At the same time, the economics of American AI begin to wobble: revenue moats built on proprietary access erode, and developers, seeking speed and cost, increasingly adopt Chinese toolchains and defaults. Around the edges, a dual-use shadow forms, as civilian and military applications diffuse together in ways that no export-control regime can meaningfully trace. These forces accumulate not through spectacle, but through quiet inevitability, yielding a geopolitical outcome Washington has long feared: an erosion of strategic advantage, not by confrontation, but by encirclement.